DNS DoS again #net
A little over a month ago my DNS servers for asjo.org were getting a lot of traffic - I never figured out why, but it was enough to bring my home router to its knees.
The same thing happened today - I noticed because my jukebox kept rebooting, because it couldn't ping the router and assumed that it itself had fallen off the network.
But it hadn't, the router was just swamped and not answering:
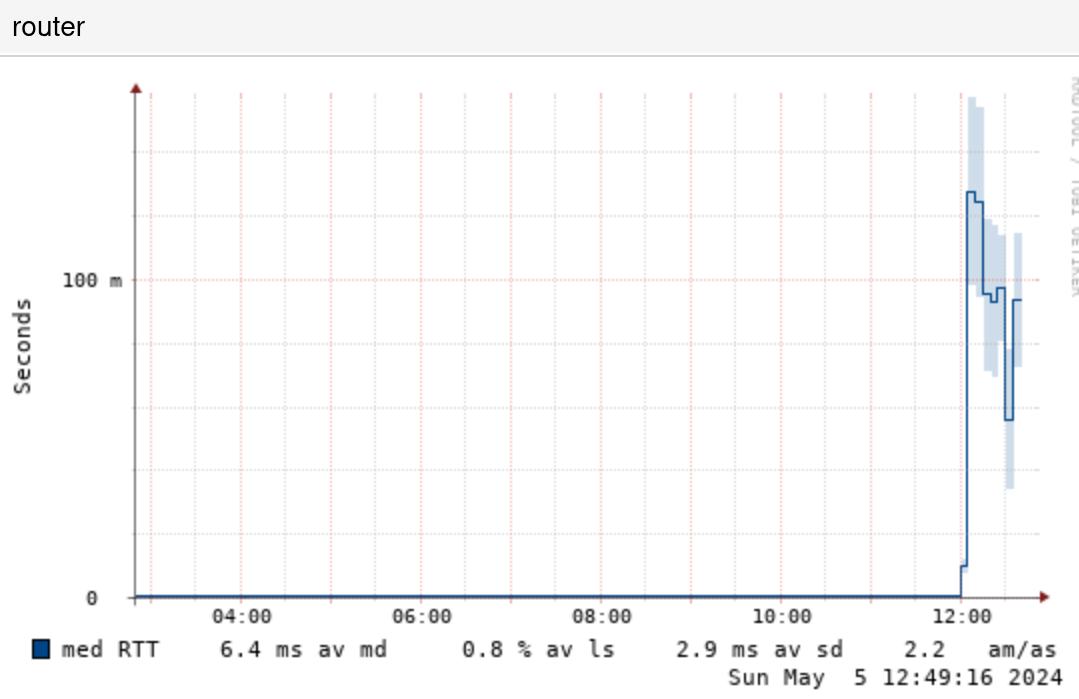
The cause seems to be the same as he last time, one IP address located
in China sending an eccessive amount of udp DNS requests for
asjo.org. Litteraly 998/1000 packets were that.
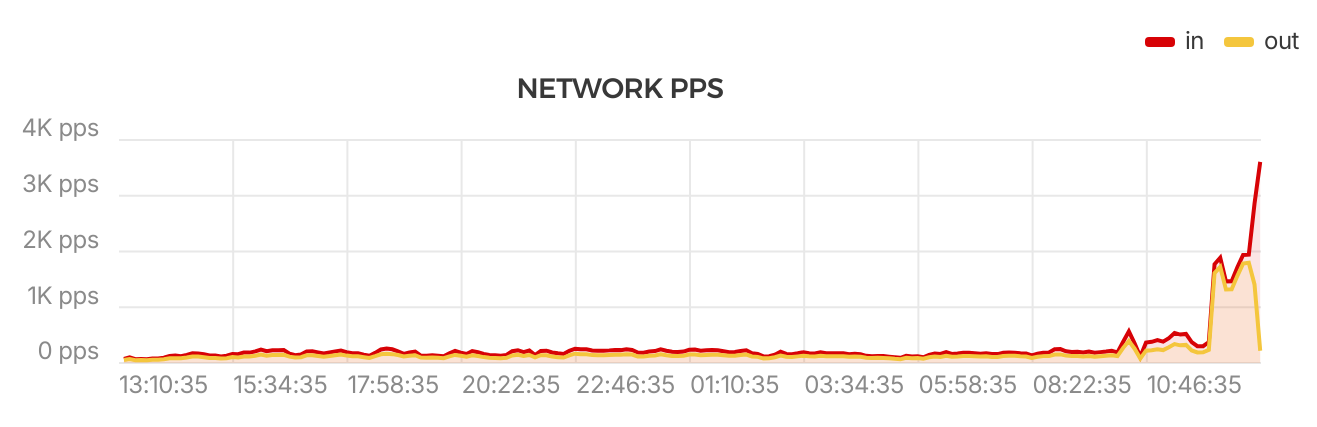
Looking at the two other DNS servers clearly shows that they were being hit as well:

On this one you can see the outgoing graph plunging after I added an iptables rule to DROP packets coming from the offending IP-address, no more answers for you:
I couldn't get to the firewall interface in the router as it was too overloaded - so I had to reboot it, and then I was able to add this second IP-address to my "Drop DNS flood"-rule, and then smokeping started looking much better:
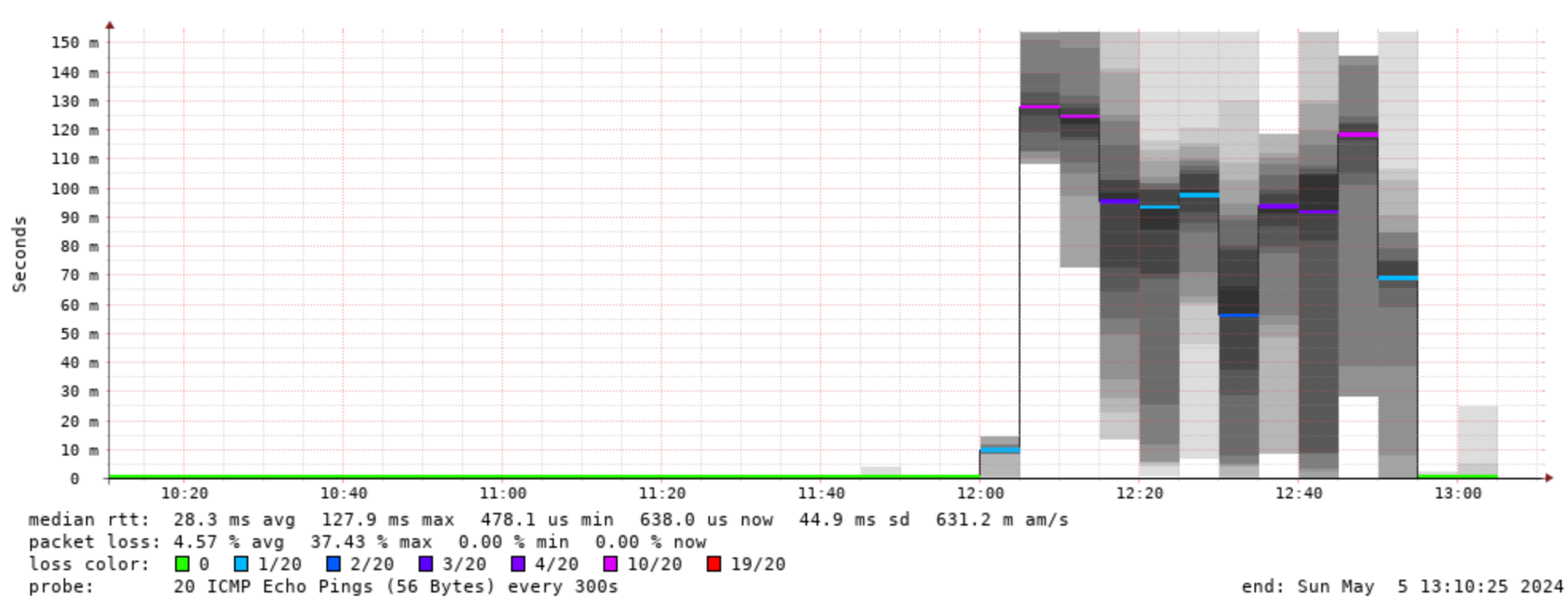
I still have no idea what the reason for these low-key DoS attacks are.

Add comment
To avoid spam many websites make you fill out a CAPTCHA, or log in via an account at a corporation such as Twitter, Facebook, Google or even Microsoft GitHub.
I have chosen to use a more old school method of spam prevention.
To post a comment here, you need to:
- Configure a newsreader¹ to connect to the server
- Open the newsgroup called
¹ Such as Thunderbird, Pan, slrn, tin or Gnus (part of Emacs).koldfront.dkon port1119using nntps (nntp over TLS).lantern.koldfrontand post a follow up to the article.Or, you can fill in this form: